Introduction
As more people turn to the internet and blockchain technology for their day-to-day lives, opportunistic criminals have also found novel ways to poison the websites and devices used. One of these threats to users is cryptojacking, a kind of cyberattack that can make use of the target’s computing power to illicitly mine cryptocurrency.
Definition: Cryptojacking is a cybercrime that involves a bad actor gaining unauthorized access to a mobile device or computer and employs measures to mine cryptocurrency.
Since crypto mining requires the solving of tedious and resource-consuming arithmetic equations, hackers turn to cryptojacking to target devices and networks to make up for inadequate mining resources. A successful attack makes available resources that can be used to mine cryptocurrency at a rate equal to the resources hacked.
How does cryptojacking work?
With the rise of cryptocurrencies, cryptojacking has seen a steady uptrend. A popular attack called the WannaCry worm attack in 2017 affected several systems on several continents. In this attack, hackers encrypted files on users’ systems and requested Bitcoin ransom to decrypt the files.
At the basic level, this attack harnesses the victim’s computing power and resources. The hacker then utilizes the hijacked computing resources to mine cryptocurrencies.
The newly minted cryptocurrencies are deposited to the hacker’s wallet while the costs (e.g. electricity tariffs and heating of the mining machines) are the victim’s burden.
There are two popular strategies employed by attackers to carry out crypto mining:
1. Download
This method requires psychological and social engineering hacking methods that lure the victim into loading the crypto mining code on their devices. Phishing emails that look legitimate may be sent to victims, urging them to click on a link that runs malicious code on their device. This code then runs in the background without the victim’s knowledge.
2. Injection
In this strategy, the malicious code is hosted on online ads and websites. The victim only needs to view the website or ad for their computers to be infected. The victim’s system doesn’t store any code for this strategy to activate.
In both methods, the malicious code solves the mathematical equations required to mine the cryptocurrencies and passes the results of these equations to the hacker’s controlled server.
There’s a third strategy, called the “hybrid method,” that combines the above. An attack may target 100 computers, with 90 infected with the code and the remaining ten receiving it via web browsers.
How does Cryptojacking work?
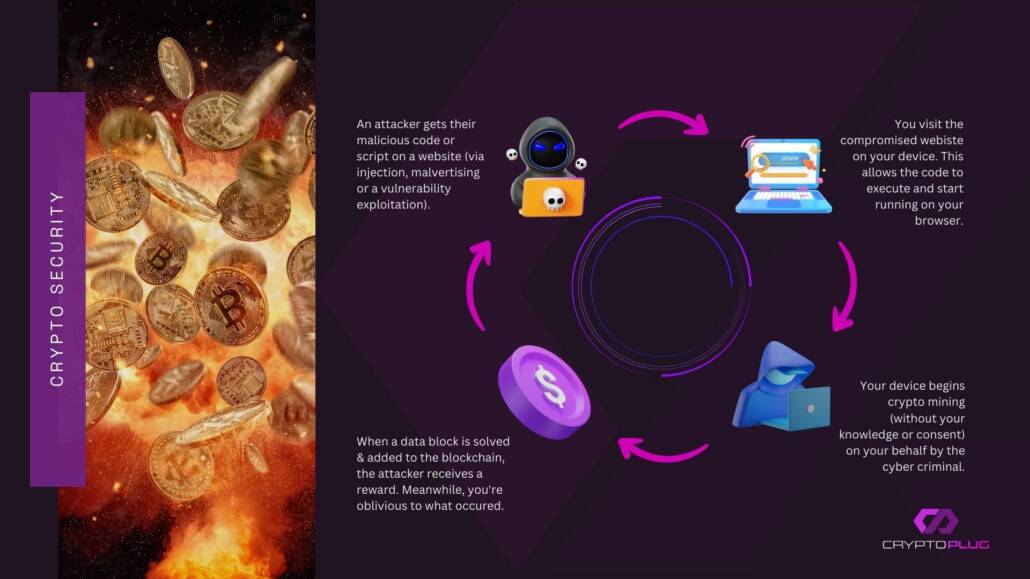
Here are the steps involved in the cryptojacking process:
- Compromising an asset: this simply means an attack embedded their malicious code in their target’s systems.
- Execution of code: the attack then waits for their victim to execute the code. This can be done by clicking on an attachment or link or visit a website with an infected ad that executes and runs the code.
- Attack activated: once the code is ran, the crypto mining script will begin to run in the background without the victim’s knowledge.
- Script solves algorithm: the malicious script then utilises the computer power of the victim’s device to solve the complex mathematical equations required to mine the cryptocurrency.
- Receive reward: When a new cryptocurrency is mined, the hacker receives the coins in their digital wallet as a reward.
Notable examples of Cryptojacking
Yahoo!
December 2013 saw Yahoo! Europe host an ad containing Bitcoin mining malware that infected an estimated two million computers within four days. The software was called Sefnit.
WannaMine
In February 2018, Panda Security, a Spanish security firm, notified the public of cryptojacking called “WannaMine.” The malware was said to have spread to several computers around the globe. It maintained persistence on host systems by generating a.dll and service name based on a list of hard-coded strings. The malware was used to mine Monero.
Coinhive
Later in February 2018, a cryptojacking attempt that exploited a vulnerability in text-to-speech software installed on the websites of the governments of Britain, the United States, and Canada had an effect on these countries. In order to mine Monero using website users’ browsers, attackers injected the Coinhive script into the program.
Tesla
Also in February 2018, Tesla Inc. discovered that it had been a victim of cryptojacking. Its Amazon Web Services cloud infrastructure was running malicious code. However, the attack was minimal.
The Microsoft Attacks
In 2019, the Microsoft Store identified eight apps used for cryptojacking. Though the apps were promptly removed, the damage was already done. There were speculations that the apps were developed by different developers, but it was concluded that one person or an organization was responsible.
The attack was also used to mine Monero. The infected apps corrupted JavaScript codes and slowed down the performance of affected devices.
In 2021, Microsoft Exchange servers hosted multiple zero-day vulnerabilities that allowed remote code execution. This vulnerability was used to mine cryptocurrency.
The European Department Attack
The Central Water Control System of Europe was used to mine Monero in 2018. The hackers infected the key operating system of the entire water utility network.
Los Angeles Times
The leading American media house was attacked in 2018, and the report page was targeted. Anyone who accessed this page on their mobile phones or data-driven devices was infected. This attack lasted a long time and allowed hackers to mine Monero.
How common are cryptojacking attacks?
Cryptojacking attacks have steadily increased over the years. According to the report titled “2022 SonicWall Cyber Threat Report,” cryptojacking attacks soared by 30% to 66.7 million in the first half of 2022.
“Despite a precipitous drop in the price of cryptocurrency, global cryptojacking volume rose to 66.7 million in the first half of 2022, up 30% over the first half of 2021. The number of attacks on the finance industry is five times greater than the second highest industry — retail, which used to be at the very bottom of the list,” the report noted.
Cryptojacking incidences have continued to rise, according to SonicWall experts, despite a significant decline in Bitcoin prices since January 2022, demonstrating that such incidents persist despite market swings. The researchers also claimed that the increase was caused by the increased enforcement against ransomware assaults, which made cryptojacking their go-to method for illegal mining.
Effects of Cryptojacking
A cryptojacking attack on an individual may result in higher electricity bills and slow computers. For enterprises though, the impact can be significant. Downtime caused by slow computers and poor servers can cost companies huge financial losses and can damage their reputation.
Here are things to look out for:
Poor performance
The success of a cryptojacking attack rests on how much the code consumes the targeted device’s resources. A sudden dip in the productivity of a computer indicated by a downslope in its performance chart is a sign of cryptojacking.
The attack significantly reduces the performance of the device by heaping the burden of mining on it. This slows the processing capabilities, shuts down the system, and causes crashes in apps or failures to open them.

Sudden heat
Cryptojacking can overburden the device’s operating system, causing it to overheat. Though overheating is common and can be for entirely different reasons, it’s better to investigate and look at other cryptojacking signs.
CPU usage
When visiting a website with little to no media content, a rise in CPU utilization could indicate the presence of cryptojacking scripts. Checking your device’s central processing unit (CPU) used in the Activity Monitor or Task Manager is a good cryptojacking test.
Prevention Methods
Use cybersecurity apps
Using anti-virus applications or cybersecurity programs can significantly help to detect threats and provide malware protection against malicious codes.
Use anti-cryptojacking browser extensions
Cryptojacking scripts are deployed using web browsers. As a result, extensions such as minerBlock, No Coin, and Anti Miner can be useful in blocking cryptojackers.
Ad blockers
Many ads on several websites may carry cryptojacking scripts. Cryptojacking scripts can be detected and blocked by Ad Blockers Plus.
Educate IT teams and other employees
For companies, IT teams need to be trained on the latest cryptojacking trends. They should be educated on how to detect, investigate, and stop cryptojacking attempts before they escalate.
Employees need to be made aware of these signs that can compromise cybersecurity because IT staff rely on them to alert them when systems are running slowly or becoming too hot. They must be taught not to click on unrelated links in emails unless they come from a reliable source. The same holds true for private emails.
Disable JavaScript
When browsing online, disabling JavaScript can help prevent cryptojacking codes from infecting your system. This may also affect other functions that are required while browsing.
Conclusion
Cryptojacking attacks are like other types of cybercrime—the goal is profit. The vulnerability of online systems that are data-driven cannot be overemphasized. It’s on internet users to be careful of what sites or emails they open. Vigilance is important in preventing this type of attack.


